Alphabet Inc, the parent company of Google is likely to acquire a cybersecurity startup Wiz for USD $23 billion and…
This week on the Lock and Code podcast… Full-time software engineer and part-time Twitch streamer Ali Diamond is used to…
The two central London NHS Trusts affected by the Qilin ransomware attack on pathology lab partner Synnovis are still cancelling…
The SEXi ransomware operation, known for targeting VMware ESXi servers, has rebranded under the name APT INC and has targeted…
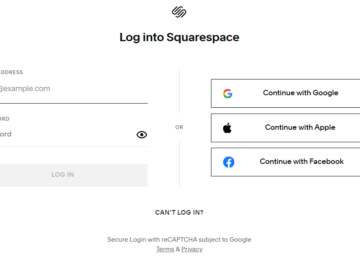
At least a dozen organizations with domain names at domain registrar Squarespace saw their websites hijacked last week. Squarespace bought…
New Poco RAT Malware Targets Spanish Speakers Through Emails! Disguised as financial documents, Poco RAT steals your info & hijacks…
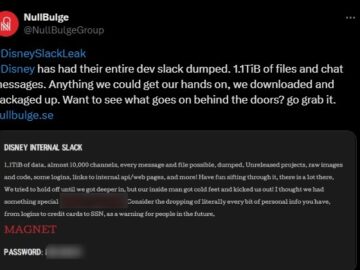
A group of cybercriminals going by the handle NullBulge claims to have downloaded the Slack channels used by Disney’s developers….
Microsoft has confirmed that Windows Server updates from last month’s Patch Tuesday break some Microsoft 365 Defender features that use the network…
Pinterest, the popular image-sharing platform with over 518 million monthly active users, faces a potential data leak that could affect…
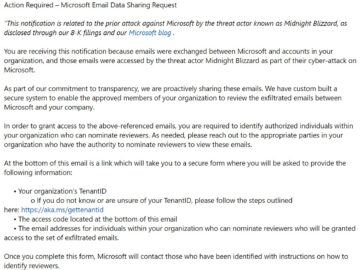
Microsoft recently sent data breach notifications to Microsoft 365 customers that were flagged as spam and even blocked by the…
Hackers focus on Juniper Junos because it is extensively used in business networking and, consequently, a huge target for hacking…
A hacktivist group claims to have hacked into renowned entertainment company Disney’s internal Slack channels and stolen about more than…