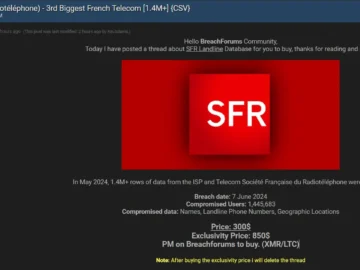
Societe Francaise Du Radiotelephone, popularly known as SFR, a prominent telecommunications company based in France, has fallen victim to an…
A pro-Houthi group, OilAlpha, is targeting humanitarian organizations in Yemen with malicious Android applications by stealing credentials and gathering intelligence,…
A Houthi-aligned group has been deploying Android surveillanceware called GuardZoo since October 2019 to target military personnel in the Middle…
July 12, 2024 – In a new malware campaign, threat actors are using Google ads to target Mac users looking…
Jul 15, 2024NewsroomCybersecurity / Mobile Security Retail banking institutions in Singapore have three months to phase out the use of…
A senior civil servant on the Post Office board said subpostmasters were “sabre-rattling” when, in 2015, they announced they were…
AT&T admitted on Friday that a significant security breach had compromised the call records of tens of millions of its…
Imagine waking up to discover that hackers have breached your company’s defenses, accessed sensitive customer data and crippled your operations….
The threat actor Crystalray, previously observed using SSH-Snake, has significantly expanded operations, targeting over 1,500 victims. Employing mass scanning, exploiting…
The Monetary Authority of Singapore (MAS) and The Association of Banks in Singapore (ABS) announced today that major retail banks…
BianLian emerged in 2022, and after its emergence rapidly, it became one of the three most active ransomware groups. They…
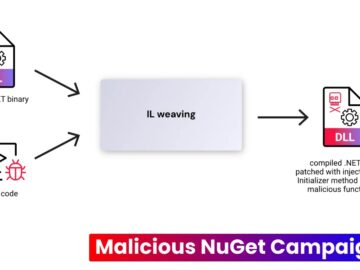
Hackers often target NuGet as it’s a popular package manager for .NET, which developers widely use to share and consume…