A new threat has surfaced in the mobile banking landscape Herodotus, a sophisticated Android banking Trojan that has been wreaking…
A new scam is tricking cryptocurrency users into giving away their funds by promising instant, massive profits. The scheme targets…
Nov 07, 2025Ravie LakshmananSupply Chain Attack / Malware A set of nine malicious NuGet packages has been identified as capable…
Cisco fixes critical UCCX flaw allowing Root command execution Pierluigi Paganini November 07, 2025 Cisco patched a critical flaw in…
Rapid7 Pros Correlates web app vulnerabilities with underlying infrastructure risk and active threat data. Provides expansive enterprise discovery of unknown…
A sophisticated phishing campaign is actively targeting hotel establishments and their guests through compromised Booking.com accounts, according to research uncovered…
The Congressional Budget Office (CBO), which serves as Congress’s official financial advisor, has been targeted in a suspected cyberattack by…
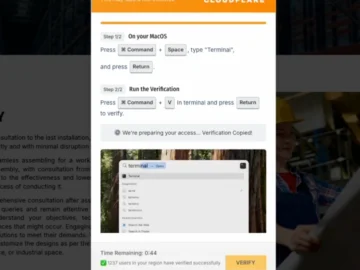
Attackers have taken the ClickFix technique further, with pages borrowing tricks from online sellers to pressure victims into performing the…
The C-suite is caught in an AI pressure cooker. On one side, boards and CEOs see the relentless headlines of…
ESET Research Threat Reports An overview of the activities of selected APT groups investigated and analyzed by ESET Research in…
China-linked threat actors have intensified their focus on influencing American governmental decision-making processes by targeting organizations involved in shaping international…
“What is recommended is that when something happens, they go to open the folder and the next day request the…