AT&T is warning of a massive data breach where threat actors stole the call logs for approximately 109 million customers,…
Hackers use Banking Trojans to steal sensitive financial information. These Trojans can also intercept and modify transactions, allowing hackers to…
Hacktivist group NullBulge claims to have breached Disney, leaking 1.1 TiB of internal Slack data. The leak allegedly includes messages,…
APIs are at the core of modern technology stacks, and power organizations’ digital operations. Facilitating seamless connections between customers and…
In this Help Net Security, Ashley Harrington, Director of Cybersecurity at Aspida, discusses the impact of cyberattack on business operations…
In April 2024, we reported how Apple was warning people of mercenary attacks via its threat notification system. At the…
Jul 12, 2024The Hacker NewsDigital Security / Online Safety In today’s digital age, passwords serve as the keys to our…
Howdens, which supplies kitchens to tradespeople, has developed a new artificial intelligence (AI)-powered app to provide technical knowledge. Chip uses…
Researchers have discovered a new have a new weapon on the dark web markets: FishXProxy, a sophisticated phishing toolkit that’s…
Smishing Triad Is Targeting India To Steal Personal and Payment Data at Scale Pierluigi Paganini July 12, 2024 Resecurity has…
Image: MidjourneyNetgear warned customers to update their devices to the latest available firmware, which patches stored cross-site scripting (XSS) and…
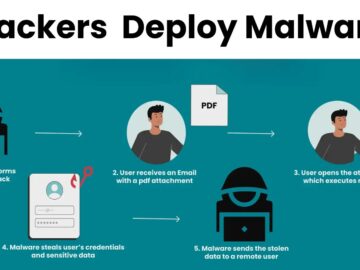
Cybersecurity researchers at McAfee Labs have uncovered a sophisticated new method of malware delivery, dubbed the “ClickFix” infection chain. This…