From targeted wiretaps to bulk surveillance dragnets, phone companies have been at the center of privacy concerns for decades—and their…
RALEIGH, NC—Advance Stores Company, Incorporated, a prominent commercial entity in the automotive industry, has recently been the victim of a…
AT&T confirms a data breach exposing call and text records for “Nearly All” customers from May 2022 to October 2022….
Cyberthreats never stay the same. Just as fast as cybersecurity providers shut down an attack vector or develop a fix…
13 Jul AT&T Data Breach Poses Phishing Attack Risk To Consumers Posted at 09:20h in Blogs by Di Freeze This…
Personal information of over 2,3 million individuals has been stolen by attackers as part of the massive data grab via…
In a new episode of Spy vs Spy, the mobile monitoring app mSpy has suffered a data breach that exposed…
Jul 12, 2024NewsroomMalware / Cyber Attack Cybersecurity researchers have shed light on a short-lived DarkGate malware campaign that leveraged Samba…
High-profile cyber attacks and data breaches that make headline news have done much to increase awareness of security issues among…
A critical Exim vulnerability in the widely-used Exim mail transfer agent (MTA) has recently been disclosed, potentially affecting over 1.5…
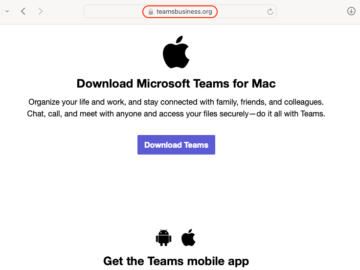
A sophisticated malvertising campaign is targeting Mac users searching for Microsoft Teams, highlighting the growing competition among malware creators in…
Australia plans to introduce a law by the end of the year forcing internet companies to proactively stop hosting scams…