The Japan Aerospace Exploration Agency (JAXA) has revealed details of a cybersecurity incident that occurred last year, involving unauthorized access…
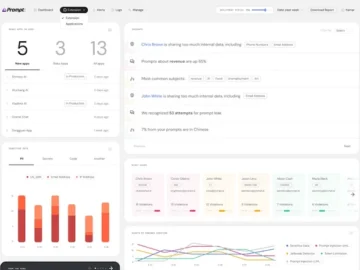
Prompt Security announced its product and go-to-market support for Managed Security Service Providers (MSSPs). This strategic initiative has already resulted…
In the shadows of the internet lurks a sophisticated web of deception and exploitation, primarily centered around a practice known…
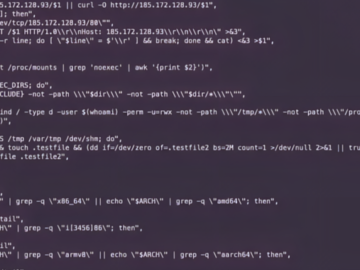
A threat actor has claimed to possess unauthorized access to Fortinet VPNs of over 50 organizations in the United States….
A critical vulnerability in PHP, tracked as CVE-2024-4577, is being actively exploited by threat actors in wild just days after…
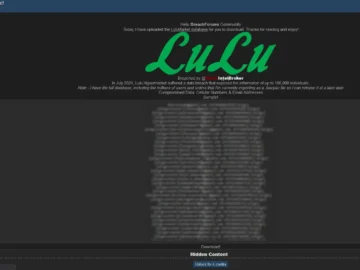
IntelBroker, a solo hacker on dark web forums, has claimed the LuLu Hypermarket data breach, targeting a prominent retail giant…
Jul 11, 2024NewsroomCyber Attack / Vulnerability Multiple threat actors have been observed exploiting a recently disclosed security flaw in PHP…
With terms like “AI washing” making their way into mainstream business consciousness, the hype surrounding AI is making it harder…
In this Help Net Security interview, Chaim Mazal, Chief Security Officer at Gigamon, discusses cybersecurity preparedness measures for businesses, the…
Jul 11, 2024NewsroomSoftware Security / Vulnerability GitLab has shipped another round of updates to close out security flaws in its…
This article compiles excerpts from various reports, presenting statistics and insights that could be helpful for CISOs. CISOs becoming more…
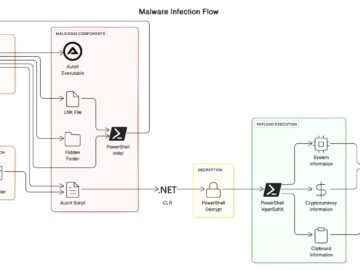
Researchers have observed improvements in the ViperSoftX info-stealing malware that had been first spotted in 2020. The malware has moved…