In the two weeks since the U.S. Supreme Court struck down a 40-year-old precedent that gave federal agencies wide latitude…
Non-profit Catholic Healthcare is using Microsoft’s holographic headset HoloLens to carry out telehealth appointments between residential care nurses and remote…
Over the last month, Microsoft 365 and Microsoft Office users have been experiencing “30088-27” errors when attempting to update the application….
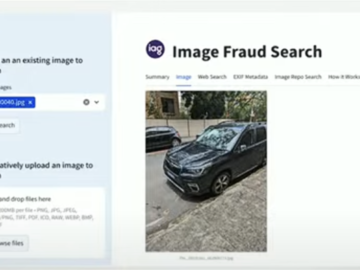
IAG is working with Google Cloud on a way to detect whether photos submitted as part of an insurance claim…
A large-scale fraud campaign with over 700 domain names is likely targeting Russian-speaking users looking to purchase tickets for the…
Advanced Micro Devices (AMD) will acquire Finnish artificial intelligence startup Silo AI for about US$665 million ($985 million) in cash…
Japan’s Computer Emergency Response Team Coordination Center (JPCERT/CC) is warning that Japanese organizations are being targeted in attacks by the…
Lulu Hypermarket has experienced a major data breach, exposing over 200,000 customer records. The attack, claimed by IntelBroker hackers, includes…
McGrath Estate Agents has lost its head of technology Darren Warner after a two-year stint that included a digital transformation…
The seemingly legitimate online marketplace Huione Guarantee is being used as a platform for laundering money from online scams, especially…
Evolve Bank & Trust, a financial institution with both traditional banking and open banking services, disclosed a data breach impacting…
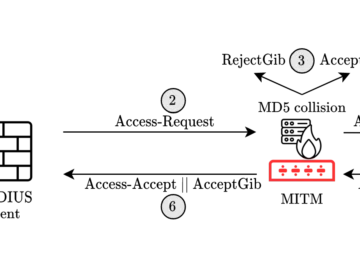
A critical vulnerability in the widely used RADIUS authentication protocol could allow attackers to gain unauthorized access to networks and…