Microsoft has given up its board observer seat at OpenAI in a move aimed at easing US and UK antitrust…
GitLab warned today that a critical vulnerability in its product’s GitLab Community and Enterprise editions allows attackers to run pipeline…
The latest variants of the ViperSoftX info-stealing malware use the common language runtime (CLR) to load and execute PowerShell commands…
Information security policies are a table-stakes requirement for any significantly sized organization today but too often they are a mess…
CISA and the FBI urged software companies on Wednesday to review their products and eliminate path OS command injection vulnerabilities…
The history of artificial intelligence (AI) is a fascinating journey of innovation and discovery that spans decades. From the early…
The civil servant on the Post Office board during subpostmasters’ High Court litigation battle has said he was alone in…
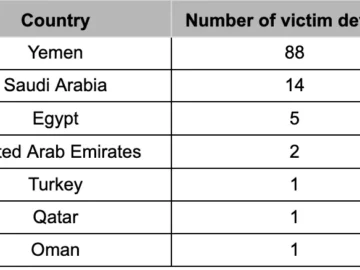
Cybersecurity researchers observed an Android surveillance campaign active since October 2019 that has targeted the military personnel of various countries…
Monzo is launching its public bug bounty program, a strategic step to bolster online security. With a keen focus on…
Microsoft fixed a Windows zero-day vulnerability that has been actively exploited in attacks for eighteen months to launch malicious scripts…
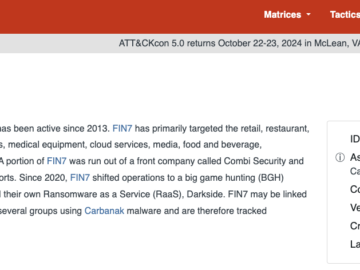
The Russia-based cybercrime group dubbed “Fin7,” known for phishing and malware attacks that have cost victim organizations an estimated $3…
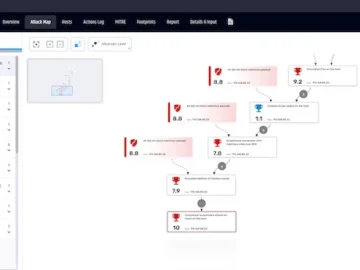
Pentera announced a major update to its RansomwareReady product, enabling customers to proactively test the security of their Linux environments….