Evolve Bank & Trust, a prominent financial services institution, has confirmed a data breach that has compromised the personal information…
Millions of Legal Documents Exposed Online! Sensitive data leak raises security concerns for the legal industry. Learn how this breach…
An investment company that had several proposals to build new datacentres in the south of England rejected by local planning…
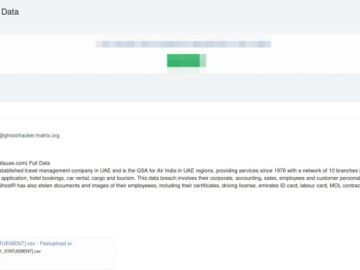
A threat actor known as “ghostr” on the XSS forum has claimed responsibility for a significant data breach targeting the…
A new flaw in OpenSSH can lead to remote code execution Pierluigi Paganini July 10, 2024 A vulnerability affects some…
Adobe has released crucial security updates for its widely-used software products: Premiere Pro, InDesign, and Bridge. The updates, identified as…
Scammers no longer need to possess technical expertise or devise intricate fraud schemes. The rise of Fraud-as-a-Service (FaaS) has revolutionized…
On the second Tuesday of July 2024, Microsoft Corporation issued its latest round of security updates, marking another Patch Tuesday…
Nokia Corporation, a prominent Finnish telecommunications and technology company, reportedly fell victim to a data breach. According to reports on…
A significant data breach involving Microsoft has come to light, exposing sensitive information of over 2,000 employees. The Cyber Press…
Jul 10, 2024NewsroomOnline Scam / Blockchain Cryptocurrency analysts have shed light on an online marketplace called HuiOne Guarantee that’s widely…
The City of Philadelphia has disclosed about data breach that occurred in May 2023, impacting the personal information of 35,881…