CISO HoneyBook | Israel | On-site – View job details As a CISO, you will develop and implement a multi-year…
A new security vulnerability has been discovered within select versions of the OpenSSH secure networking suite, potentially exposing systems to…
Polyfill.io helps web developers achieve cross-browser compatibility by automatically managing necessary polyfills. By adding a script tag to their HTML,…
Technologies such as GenAI, ML and IoT are giving threat actors new tools that make it easier to target consumers…
In this Help Net Security interview, Jake King, Head of Threat & Security Intelligence at Elastic, discusses companies’ exposure to…
Jul 10, 2024NewsroomVulnerability / Network Security Select versions of the OpenSSH secure networking suite are susceptible to a new vulnerability…
Fujitsu Limited has disclosed the results of an investigation into a cyberattack that potentially exposed customers’ personal information. The breach,…
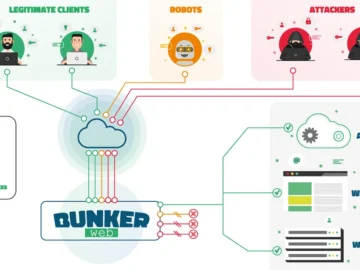
BunkerWeb is an open-source Web Application Firewall (WAF) distributed under the AGPLv3 free license. The solution’s core code is entirely…
A proof-of-concept (PoC) exploit has been released for a critical local file inclusion vulnerability in Splunk Enterprise, identified as CVE-2024-36991….
73% of security professionals admit to using SaaS applications that had not been provided by their company’s IT team in…
The City of Philadelphia revealed that a May 2024 disclosed in October impacted more than 35,000 individuals’ personal and protected…
Microsoft plugs critical security holes in July Patch Tuesday! 142 vulnerabilities patched, including actively exploited zero-days and remote code execution…