The financial results of the world’s biggest three hyperscale cloud companies have seen Amazon, Google and Microsoft all credit growing…
Hackers are trying to exploit a vulnerability in the Modern Events Calendar WordPress plugin that is present on more than 150,000 websites…
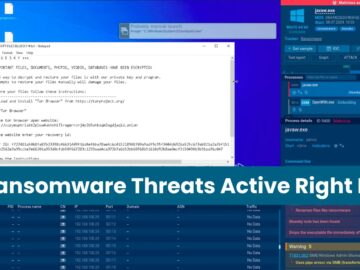
Group-IB researchers report a sharp rise in Eldorado – Golang-based ransomware with cross-platform encryption- operations, targeting various industries. Learn how…
Since the SEC’s updated Cybersecurity Disclosure rulings came into force in December, unsuspecting CISOs have seen a sudden shift in…
The current computing curriculum is so focused on programming skills that other essential digital skills are left by the wayside,…
Ransomware continues to loom large over the cybersecurity landscape, causing significant damage to individuals and organizations alike. With the difficulty…
The human element is one of the biggest reasons why data breaches have risen in recent years. And even though…
The China-backed advanced persistent threat (APT) actor tracked as APT40 has been busy evolving its playbook and has recently been…
Australian Home Affairs Secretary Stephanie Foster has initiated a new initiative across commonwealth agencies aimed at fortifying Commonwealth cybersecurity against…
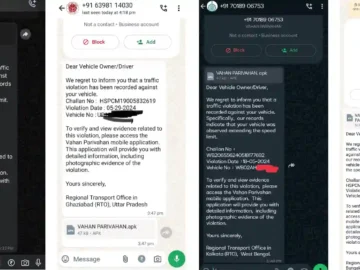
Cyble Research and Intelligence Labs (CRIL) researchers have observed a new campaign in which threat actors claiming to be from…
Phylum uncovers large-scale trojanized jQuery attacks targeting npm, GitHub, and CDNs. Malicious actors steal user form data through a modified…
CISA’s recent guidance to shift from VPNs to SSE and SASE products strengthens data protections, but misses an opportunity to…