For enterprises that want to extend their storage strategy, the public cloud is a place to start that can bring…
Remediating Vulnerabilities Streamlining communication between hackers and security teams, HackerOne customers are able to quickly and thoroughly remediate vulnerabilities before…
A joint advisory from international cybersecurity agencies and law enforcement warns of the tactics used by the Chinese state-sponsored APT…
Configuration drift happens when the configurations of storage & backup systems and software deviate from a baseline or standard configuration…
A new critical security vulnerability in the RADIUS protocol, dubbed BlastRADIUS, leaves most networking equipment open to Man-in-the-Middle (MitM) attacks….
While cybercriminals are offering free tickets to Taylor Swift Eras Tour and other events, Ticketmaster is telling would-be purchasers that…
Hamas hacked into video streams from private security cameras in Israeli homes to gather intelligence before fighters descended on Israeli…
Evolve Bank & Trust (Evolve) is sending notices of a data breach to 7.6 million Americans whose data was stolen…
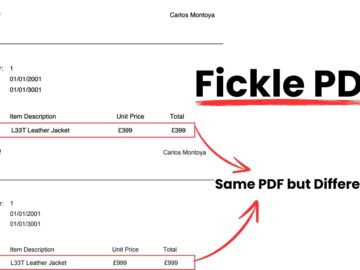
A cybersecurity researcher, Zakhar Fedotkin, demonstrated how differences in PDF rendering across various browsers and operating systems can be exploited…
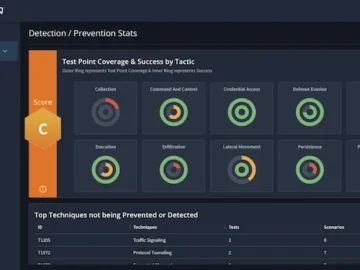
AttackIQ has introduced a new functionality for enterprise customers – AttackIQ Mission Control. AttackIQ Mission Control enhances AttackIQ Enterprise BAS…
Jul 09, 2024NewsroomVulnerability / Network Security Cybersecurity researchers have discovered a security vulnerability in the RADIUS network authentication protocol called…
Flash storage pioneer Pure Storage recently announced it will upgrade its Fusion control plane to make storage capacity in its…