Microsoft reminded customers today that multiple editions of Windows 11, version 22H2, will reach the end of servicing (EOS) in…
Ticketmaster hackers leak 30,000 ticket barcodes for top upcoming events, including music concerts. They also share a DIY counterfeit tutorial…
Security researchers discovered a new sophisticated cyberespionage tool targeting Russian government entities in May 2024. The tool, dubbed CloudSorcerer, exploits…
Apple has removed 25 virtual private network (VPN) apps from the Russian App Store at the request of Roskomnadzor, Russia’s…
TeamViewer, the company developing the popular remote access/control software with the same name, has finished the investigation into the breach…
Microsoft has finally released a spell check and autocorrect feature in Notepad for all Windows 11 users, forty-one years after…
A remote code execution vulnerability in the Ghostscript document conversion toolkit, widely used on Linux systems, is currently being exploited…
Jul 08, 2024NewsroomCyber Espionage / Cloud Security A previously undocumented advanced persistent threat (APT) group dubbed CloudSorcerer has been observed…
Experts have warned that ageing IT equipment and infrastructure is leaving the NHS dangerously exposed to more damaging cyber breaches…
Researchers from a security firm( name withheld) have uncovered a significant data breach involving Twitter user data, revealing a leaked…
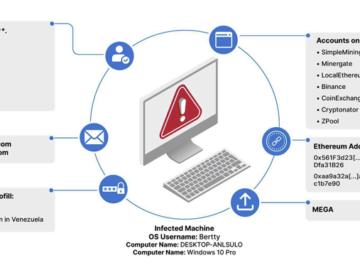
Jul 08, 2024NewsroomDark Web / Cyber Crime An analysis of information-stealing malware logs published on the dark web has led…
A new advanced persistent threat (APT) group named CloudSorcerer abuses public cloud services to steal data from Russian government organizations…