Torrance, United States / California, July 8th, 2024, CyberNewsWire AI SPERA, a leading Cyber Threat Intelligence (CTI) company, has announced…
Roblox announced late last week that it suffered a data breach impacting attendees of the 2022, 2023, and 2024 Roblox…
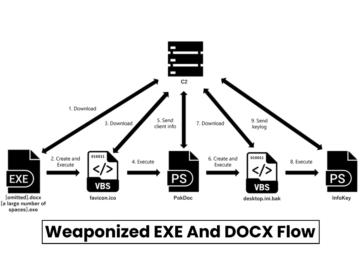
Hackers often use EXE and DOCX file formats is due to they are among the most commonly used types of…
08 Jul AI Can’t Be Our Only Defense Against AI-Generated Cyber Threats Posted at 08:56h in Blogs by Di Freeze…
Recently knighted Alan Bates has welcomed the elevation of former MP Kevan Jones – a long-time supporter of the former subpostmaster’s…
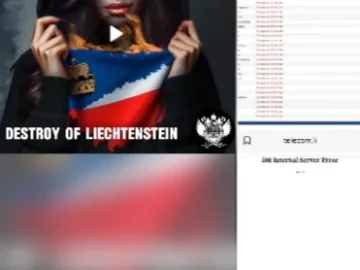
The Russian Cyber Army Team has claimed responsibility for targeting the website of Telecom Liechtenstein. This alleged Liechtenstein cyberattack was…
The role of ethical hackers in cybersecurity teams has become more crucial than ever. With the increasing complexity and frequency…
The first half of 2024 has seen a significant rise in information-stealing malware disguised as AI tools and Chrome extensions….
Apple has removed several prominent VPN service apps from the Russian division of the App Store. The affected apps include…
A major South Korean ISP is accused of installing malware on over 600,000 customers’ PCs to curb torrent traffic, raising…
Jul 08, 2024The Hacker NewsCybersecurity / Enterprise Security Events like the recent massive CDK ransomware attack – which shuttered car…
For Lyndsay Weir, the key to success with data analytics is getting to the “so what?”, beyond the charts and…