Generative AI (GenAI) is rapidly becoming an integral part of our lives and a powerful force for driving value within…
An alarming new threat has emerged targeting cybersecurity researchers. An archive containing malicious code is being distributed on the social…
A new position paper argues that Privacy Enhancing Technologies (PET) used in Home Routing are making it difficult for law…
By Ian Thornton-Trump, CISO, Cyjax “There are three ways to make a living in this business: be first, be smarter,…
Hackers attack Microsoft SmartScreen as it’s a cloud-based, anti-phishing, and anti-malware component that determines whether a website is potentially malicious,…
Jul 08, 2024NewsroomVulnerability / Software Security Four unpatched security flaws, including three critical ones, have been disclosed in the Gogs…
Manila, Philippines- 19/06/24: TraiCon Events will be hosting the Philippines’ premier cybersecurity event titled “Cyber Revolution Summit” scheduled on 10th…
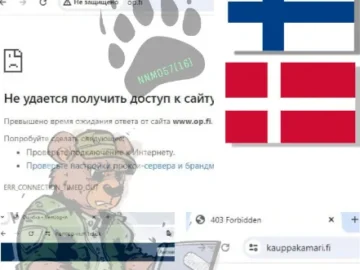
The infamous ransomware group NoName has allegedly launched cyberattacks on MitID, the Finland Chamber of Commerce, and OP Financial Group….
A newly identified multi-stage trojan, dubbed “Orcinius,” has been reported to exploit popular cloud services Dropbox and Google Docs as…
July 5, 2024 – The cybercriminals behind the Ticketmaster data breach are giving away free Taylor Swift concert tickets. July…
CISA adds Cisco NX-OS Command Injection bug to its Known Exploited Vulnerabilities catalog Pierluigi Paganini July 08, 2024 U.S. Cybersecurity…
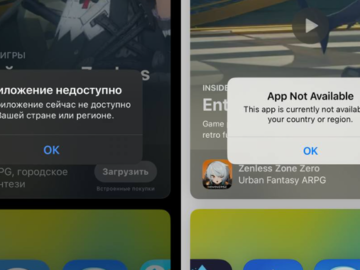
Jul 08, 2024NewsroomPrivacy / Internet Censorship Apple removed a number of virtual private network (VPN) apps in Russia from its…