The cloud holds a large – and growing – percentage of enterprise data. While much of this growth comes from…
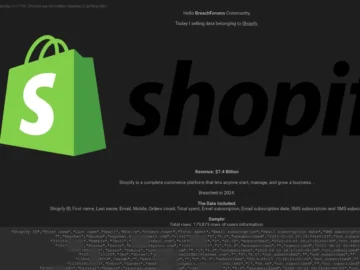
E-commerce supplier Shopify has confirmed that it did not experience a cyber security incident but stated that a data loss was…
Roblox, the globally renowned online gaming platform, has suffered a data breach. According to a tweet from cybersecurity expert H4ckManac,…
The 2024 Summer Olympic Games, also referred to as XXXIII Olympiad, are set to take place from July 26th to…
Mobile Security is increasingly crucial in today’s digital landscape, where smartphones are integral to both personal and professional lives. Samsung…
In this Help Net Security interview, Rob Greer, VP and GM of the Enterprise Security Group at Broadcom, discusses the…
Gaborone, Botswana: TraiCon Events will host Botswana’s premier cybersecurity event titled “Cyber Revolution Summit” scheduled on 9th August 2024 in…
The US celebrated Independence Day last week, providing many with a long weekend leading into patch week. With summer vacations…
Cisco has issued a security advisory regarding a critical remote code execution (RCE) vulnerability, dubbed “regreSSHion,” that affects multiple products….
Monocle is open-source tooling backed by a large language model (LLM) for performing natural language searches against compiled target binaries….
An estimated 4 million professionals are needed to fill the growing cybersecurity workforce gap, according to Fortinet. At the same…
The Australian Cyber Security Centre (ACSC)’s Essential Eight framework has the potential to transform Australia into a global leader in…