Pharmaceutical giant Cencora has confirmed that patients’ protected health information and personally identifiable information (PII) was exposed in a February cyberattack. Cencora,…
Following extensive analyses and investigations by German security authorities, the Federal Government has officially attributed responsibility for a significant cyberattack…
Miami, United States- Cyber A.I. Group, Inc., an emerging growth global cybersecurity, A.I. and IT services company, announced today that…
A ransomware attack allegedly carried out by the RansomEXX Group has reportedly affected the IT services of over 300 small…
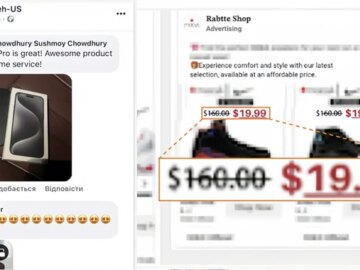
Aug 01, 2024Ravie LakshmananOnline Fraud / Malvertising Facebook users are the target of a scam e-commerce network that uses hundreds…
CrowdStrike shareholders have filed a lawsuit in the United States in which they claim the cyber security firm made materially…
Pharma Giant Cencora confirmed the theft of personal and health information Pierluigi Paganini August 01, 2024 Pharma company Cencora confirmed…
Image: MidjourneyThe Federal Bureau of Investigation (FBI) warns of scammers posing as employees of cryptocurrency exchanges to steal funds from…
A critical security vulnerability has been discovered in Bitdefender’s GravityZone Update Server, potentially exposing organizations to server-side request forgery (SSRF)…
Listing the Atomwaffen Division and the Order of Nine Angles as a lasting influence, Butcher also disclosed the nature of…
Delta Air Lines has enlisted the legal expertise of David Boies, chairman of Boies Schiller Flexner, to seek damages from…
In an alarming revelation, Kaiser Foundation Health Plan reported a data breach impacting over 13 million individuals. For years, there…