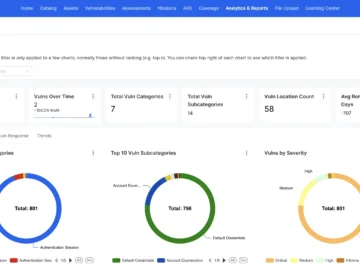
Synack has unveiled additional capabilities of its Penetration Testing as a Service (PTaaS) platform that deliver a comprehensive security testing…
How to detect and prevent attackers from using these various techniques Obfuscation is an important technique for protecting software that…
Businesses have grappled with skills shortages since the removal of free movement at the start of 2021 and the IT…
In an increasingly digital world, biometric authentication has emerged as a powerful tool for securing access to sensitive information and…
Telstra and Optus have been asked to “voluntarily” delay switching off their 3G networks by an eleventh-hour parliamentary inquiry, although…
BingoMod Android RAT steals money from victims’ bank accounts and wipes data Pierluigi Paganini August 01, 2024 BingoMod is a new…
Specula tool utilizes a Registry to turn Microsoft Outlook Into a C2 Server capable of executing arbitrary commands. Fundamentally, Specula…
Beaumont describes the RayV Lite as part of a larger trend she calls the “domestication of tooling”: Devices like the…
A recently discovered vulnerability in Bitdefender’s GravityZone Update Server has raised significant security concerns. Identified as CVE-2024-6980, this flaw allows…
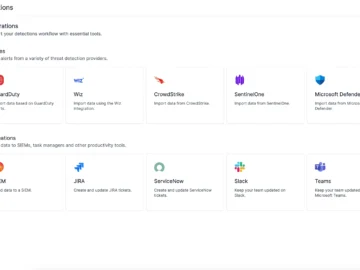
Cado Security has unveiled that the Cado platform now enables customers to dramatically streamline the effectiveness of their SOC using…
Aug 01, 2024Ravie LakshmananData Encryption / Browser Security Google has announced that it’s adding a new layer of protection to…
Now, the museum is turning its attention to the future, unveiling its new gardens in July as a centre piece…