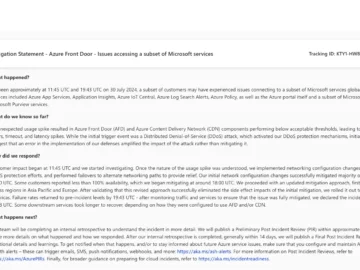
A DDoS attack that started on Tuesday has made a number of Microsoft Azure and Microsoft 365 services temporarily inaccessible,…
Jul 31, 2024Ravie LakshmananCyber Attack / Threat Intelligence Japanese organizations are the target of a Chinese nation-state threat actor that…
The Labour government is opening a consultation on its plans to reform the planning system, as part of its push…
Ransomware payments have touched a new milestone — with many hacker groups claiming large sums of ransom payments that were…
A critical vulnerability in GeoServer, an open-source Java-based software server, has put thousands of servers at risk. The flaw, CVE-2024-36401,…
Open AI says this data is used to train the AI model and improve its responses, but the terms allow…
Texas Attorney General Ken Paxton has secured a $1.4 billion settlement with Meta Platforms Inc. (formerly known as Facebook) over…
A phishing campaign targeting Donald Trump’s supporters has been launched involving fake donation websites. The campaign’s origins are still under…
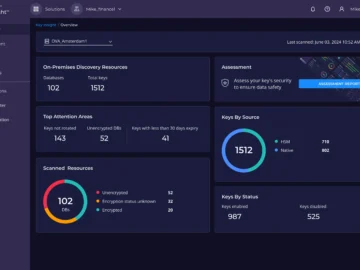
Fortanix announced a major expansion to the Key Insight solution, allowing organizations to discover, assess, and remediate their fragmented cryptographic…
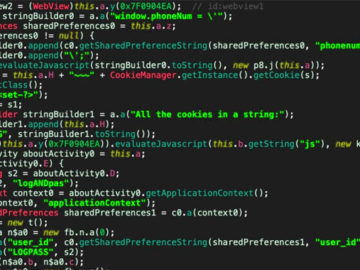
Jul 31, 2024Ravie LakshmananMobile Security / Malware A new malicious campaign has been observed making use of malicious Android apps…
Securonix, Inc., a leader in Security Information and Event Management (SIEM) and a five-time Gartner Magic Quadrant Cybersecurity leader, has…
Phishing campaigns target SMBs in Poland, Romania, and Italy with multiple malware families Pierluigi Paganini July 31, 2024 Phishing campaigns…