Experts have warned that ageing IT equipment and infrastructure is leaving the NHS dangerously exposed to more damaging cyber breaches…
Researchers from a security firm( name withheld) have uncovered a significant data breach involving Twitter user data, revealing a leaked…
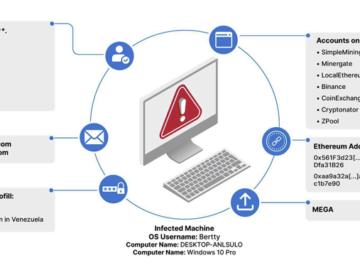
Jul 08, 2024NewsroomDark Web / Cyber Crime An analysis of information-stealing malware logs published on the dark web has led…
A new advanced persistent threat (APT) group named CloudSorcerer abuses public cloud services to steal data from Russian government organizations…
Apple removes popular VPNs from Russia’s App Store following government pressure. This move restricts access to free and open internet…
Jul 08, 2024NewsroomRansomware / Encryption An emerging ransomware-as-a-service (RaaS) operation called Eldorado comes with locker variants to encrypt files on…
Torrance, United States / California, July 8th, 2024, CyberNewsWire AI SPERA, a leading Cyber Threat Intelligence (CTI) company, has announced…
Roblox announced late last week that it suffered a data breach impacting attendees of the 2022, 2023, and 2024 Roblox…
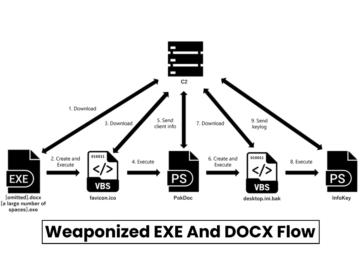
Hackers often use EXE and DOCX file formats is due to they are among the most commonly used types of…
08 Jul AI Can’t Be Our Only Defense Against AI-Generated Cyber Threats Posted at 08:56h in Blogs by Di Freeze…
Recently knighted Alan Bates has welcomed the elevation of former MP Kevan Jones – a long-time supporter of the former subpostmaster’s…
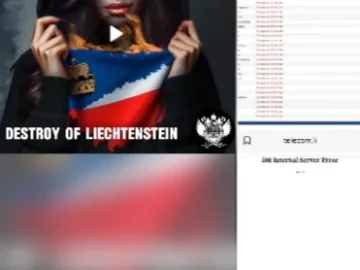
The Russian Cyber Army Team has claimed responsibility for targeting the website of Telecom Liechtenstein. This alleged Liechtenstein cyberattack was…