Most software companies resort to using third-party solutions for completing certain tasks within their company. A common example is a…
Researchers at Cyber Press discovered a 9.4GB leaked Twitter user data containing nearly 200 million user data records. This leak,…
Optimizing IT team collaboration hinges on recognizing their unique team challenges, such as siloed knowledge and communication barriers, as well…
By Neelesh Kripalani, Chief Technology Officer, Clover Infotech In today’s dynamic financial landscape, institutions are leveraging next-gen enterprise AI platforms…
Apple removed 25 VPN apps from the App Store in Russia following Moscow’s requests Pierluigi Paganini July 08, 2024 Apple…
A critical security vulnerability in MongoDB Compass, identified as CVE-2024-6376, has been discovered, potentially exposing systems to code injection attacks….
The day is slowly turning into night, and the American special operators are growing concerned. They are deployed to a…
The Egyptian Health Department (EHD) has reported a data breach affecting 121,995 individuals, including one resident of Maine. The breach,…
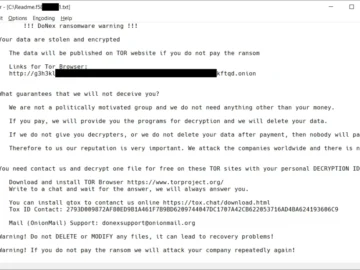
A cryptographic weakness in the DoNex ransomware and its previous incarnations – Muse, fake LockBit 3.0, and DarkRace – has…
On a popular hacking form, a user has leaked a file that contains 9,948,575,739 unique plaintext passwords. The list appears…
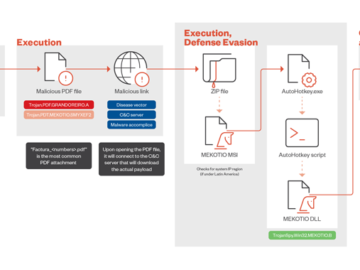
Jul 08, 2024NewsroomMalware / Cyber Threat Financial institutions in Latin America are being threatened by a banking trojan called Mekotio…
Generative AI (GenAI) is rapidly becoming an integral part of our lives and a powerful force for driving value within…