Thank you for joining! Access your Pro+ Content below. 30 July 2024 CrowdStrike blue screen bug serves a stark warning…
Cyberattacks in India have reached alarming levels, with a staggering 593 incidents reported in the first half of 2024. The…
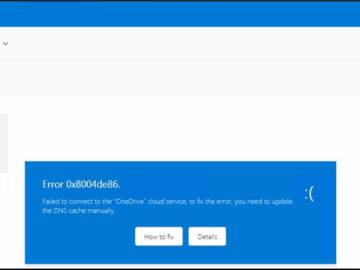
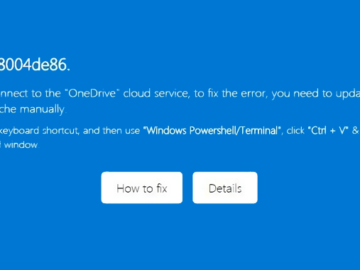
A crafty phishing campaign targets Microsoft OneDrive users Pierluigi Paganini July 30, 2024 Researchers detected a sophisticated phishing campaign targeting…
Maintaining continuous vigilance is essential for organizations of all sizes in the face of increasing cyber threats. However, lean IT…
Jul 30, 2024Ravie LakshmananCyber Espionage / Malware The nation-state threat actor known as SideWinder has been attributed to a new…
As we reflect on the Singapore cyber landscape of 2023, it’s evident that the year presented both heightened challenges and…
A grand jury in Kansas City has charged North Korean national Rim Jong Hyok for orchestrating a series of cyberattacks…
DigiCert, a leading digital certificate provider, has announced the revocation of thousands of certificates due to a domain validation error….
Jul 30, 2024Ravie LakshmananMalware / Email Security Cybersecurity researchers are warning about a new phishing campaign that targets Microsoft OneDrive…
HealthEquity, Inc., a prominent health savings account administrator, has reported a data breach affecting approximately 4.3 million individuals. The breach,…
DigiCert, a major certificate authority, to revoke thousands of SSL/TLS certificates because of a Domain Control Verification error. This could…
X, the social media platform formerly known as Twitter, is introducing a new feature that allows users to opt out…