Europol’s recent paper sheds light on formidable challenges posed by Privacy Enhancing Technologies (PET) in Home Routing systems. These technologies,…
Security breach potentially exposed internal secrets at AI research firm OpenAI after hackers accessed discussions on sensitive AI projects in…
A new ransomware-as-a-service (RaaS) called Eldorado emerged in March and comes with locker variants for VMware ESXi and Windows. The gang…
Airtel, also known as Bharti Airtel, has denied reports of a data breach following speculation from various media outlets. The…
05 Jul From Hacking Into Banks To Protecting Them, A Redemption Story Posted at 09:52h in Blogs by Di Freeze…
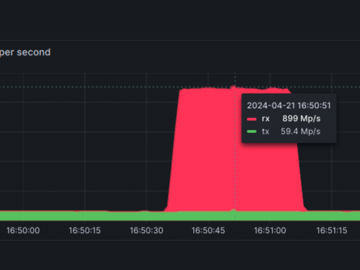
Jul 05, 2024NewsroomNetwork Security / DDoS Attack French cloud computing firm OVHcloud said it mitigated a record-breaking distributed denial-of-service (DDoS)…
As online shoppers ready themselves for the approaching Amazon Prime Day on July 16-17, 2024, a day known for unusually…
Hackers frequently target schools and bank servers to obtain important personal information, including financial data, that can be used for…
Jul 05, 2024The Hacker NewsCybersecurity / Identity Protection Identity theft isn’t just about stolen credit cards anymore. Today, cybercriminals are…
Splunk has released a comprehensive set of security updates to address 16 vulnerabilities across its Splunk Enterprise and Cloud Platform….
The Indian government has issued a high alert to the public over several fake and fraudulent emails that have been…
eSentire’s Threat Response Unit (TRU) has uncovered a sophisticated campaign where threat actors exploit the ScreenConnect remote access client to…