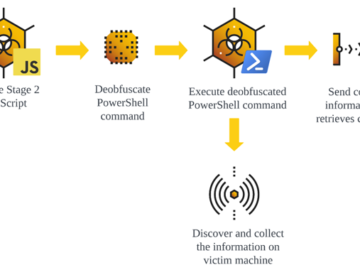
Kimsuky, also known as the Velvet Chollima, Black Banshee, THALLIUM, or Emerald Sleet, is a North Korean state-sponsored advanced cyber…
TeamViewer, the global leader in remote connectivity solutions, has provided an update on the cyber attack detected on June 26,…
4chan is ephemeral (posts are routinely culled) and supposedly anonymous (the default name setting for anyone posting is simply “Anonymous”)….
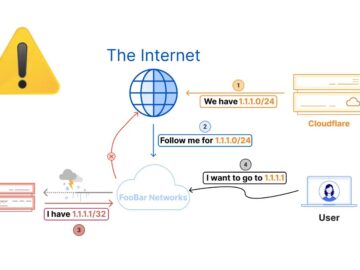
On June 27, 2024, Cloudflare experienced a disruption of its 1.1.1.1 DNS resolver service. This several-hour incident was caused by…
Leveraging Artificial Intelligence to Enhance Cybersecurity Defenses Artificial Intelligence has become essential for safeguarding digital resources in cybersecurity. As organizations…
Jul 05, 2024The Hacker NewsCloud Security / Attack Surface The attack surface isn’t what it once was and it’s becoming…
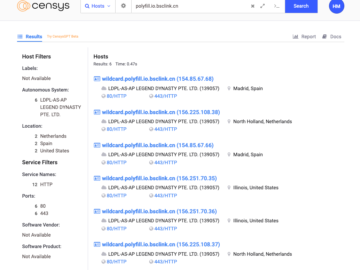
Polyfill.io Supply Chain Attack: 384,773 hosts still embedding a polyfill JS script linking to the malicious domain Pierluigi Paganini July 05,…
Hackers attack Microsoft Exchange servers because they often contain sensitive communication data that can be exploited for several illicit purposes….
Active since 2015, Mekotio is a Latin American banking trojan specifically designed to target financial data in regions like Brazil,…
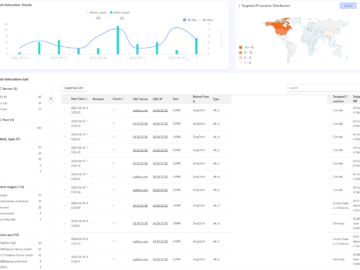
New Golang-based Zergeca Botnet appeared in the threat landscape Pierluigi Paganini July 05, 2024 Researchers uncovered a new Golang-based botnet…
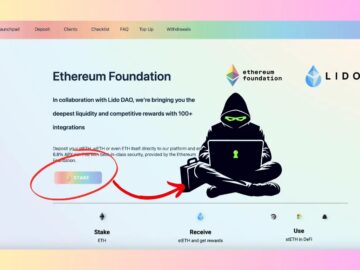
In a recent cyberattack, hackers successfully compromised Ethereum’s mailing list, attempting to drain users’ crypto funds through a sophisticated phishing…
Jul 05, 2024NewsroomSEO Poisoning / Cyber Attack, The malware known as GootLoader continues to be in active use by threat…