The Australian National University (ANU) has outlined an ambition to host an onsite quantum computer, with Fujitsu Australia to play…
Recent cyber attacks involving ransomware have garnered significant attention in recent days, with two notable incidents making headlines: Patelco Credit…
A staggering 83% of organizations have suffered a material security breach recently, with over half occurring in the past year…
A coordinated law enforcement operation codenamed MORPHEUS has felled close to 600 servers that were used by cybercriminal groups and…
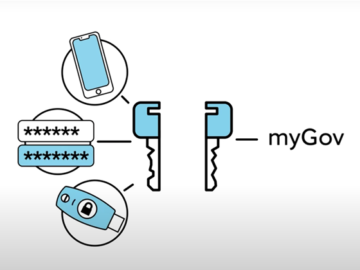
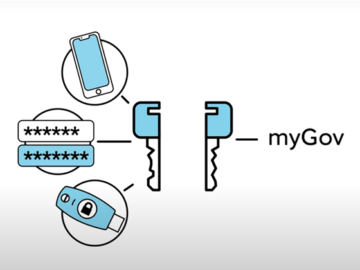
Over 20,000 myGov users have set up passkeys to log into their accounts since the capability went live last week….
In this Help Net Security interview, Mike Toole, head of security and IT at Blumira, discusses the components of an…
Jul 04, 2024NewsroomData Breach / Mobile Security Cloud communications provider Twilio has revealed that unidentified threat actors took advantage of…
Over 20,000 myGov users have set up passkeys to log into their accounts since the capability went live last week….
A critical local privilege escalation vulnerability has been discovered in MSI Center versions 2.0.36.0 and earlier, allowing low-privileged users to…
Security teams are struggling to keep pace with the risks posed by organizations’ dependency on modern applications—the technology that underpins…
The Australian government’s top secret cloud infrastructure will be built and run by AWS to host the country’s defence and…
Law enforcement agencies from around the world have successfully shut down 593 rogue servers running unauthorized versions of Cobalt Strike,…