Researchers discovered a new Android RAT (Remote Administration Tool) called SpyMax targeting Telegram users. This RAT is particularly dangerous because…
Proton has launched ‘Docs in Proton Drive,’ a free and open-source end-to-end encrypted web-based document editing and collaboration tool. Proton…
Yen says Proton has been internally using the system for the last month and is now ready to roll it…
‘Buy now, pay later’ payment specialist Affirm has warned that holders of its payment cards had their personal information exposed…
In the first half of 2024, the FakeBat loader, also known as EugenLoader or PaykLoader, emerged as a prominent threat…
American Patelco Credit Union suffered a ransomware attack Pierluigi Paganini July 03, 2024 The American credit union Patelco Credit Union shut…
Hackers have been targeting developers by using fake job offers to hijack GitHub accounts. This alarming trend has raised significant…
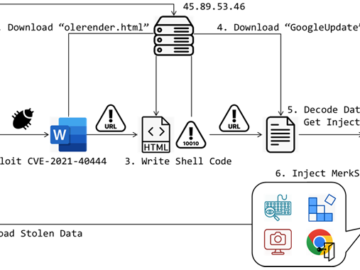
Jul 03, 2024NewsroomSpyware / Vulnerability Unknown threat actors have been observed exploiting a now-patched security flaw in Microsoft MSHTML to…
Technology sector trade body TechUK has recognised four pioneering industry leaders for their work in using digital innovation to effect…
In a collaborative effort to safeguard the integrity of the 2024 US election cycle, the Federal Bureau of Investigation (FBI),…
Affirm cardholders beware! Data breach at Evolve Bank, the issuer of Affirm credit cards, may expose personal information. Learn what…
Most video games today are typically RPGs, or role-playing games, where players immerse themselves in shooting or story-driven adventures. However,…