Microsoft has discovered and disclosed two significant vulnerabilities in Rockwell Automation’s PanelView Plus devices. These vulnerabilities could be remotely exploited…
The DDoS attacks have evolved tremendously since 2016, with Mirai-like botnets setting new records. Attack frequency and intensity increased notably…
UK-based law firm Barings has brought to light a concerning incident involving alleged cyber espionage targeting British armed personnel. According…
Splunk is a software platform designed to search, analyze, and visualize machine-generated data from various sources, including websites, applications, sensors,…
In today’s interconnected digital landscape, ransomware has emerged as one of the most pervasive and damaging cyber threats. These malicious…
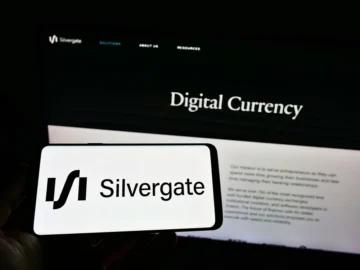
The Securities and Exchange Commission (SEC) has charged Silvergate Capital Corporation, along with its former executives Alan Lane, Kathleen Fraher,…
The Russian hacktivist alliance “Matryoshka 424” has announced the inclusion of Team ARXU, a prominent pro-Bangladeshi hacktivist group. This alliance,…
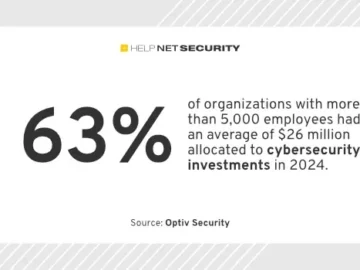
Most companies do not know how effectively they are investing money to fight the cybersecurity threat, according to Optiv. Cybersecurity…
The Australian Digital Health Agency (ADHA) is attempting to scale up its healthcare identifiers service through a new five-year roadmap….
In this Help Net Security, Martin Reynolds, Field CTO at Harness, discusses how AI can enhance the security of software…
Jul 03, 2024NewsroomMalware / Threat Intelligence An unnamed South Korean enterprise resource planning (ERP) vendor’s product update server has been…
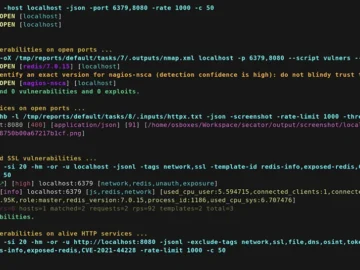
Secator is an open-source task and workflow runner tailored for security assessments. It facilitates the use of numerous security tools…