In 2022, over 24 million passwords were exposed. Are passwords becoming pointless? Even if you have one, it seems like…
By the time the Senate unanimously confirmed Nate Fick to be America’s cyber ambassador in September 2022, tech diplomacy headaches…
Hackers often mimic penetration testing services to disguise their malicious activities as legitimate security assessments. By imitating authorized security testing,…
Jul 02, 2024NewsroomHardware Security / Vulnerability Modern CPUs from Intel, including Raptor Lake and Alder Lake, have been found vulnerable…
The Florida Department of Health, the first accredited public health system in the United States, has reportedly fallen victim to…
Something needs to change with cyber security. One study found that between 2021 and 2022, data breaches increased by over…
A new Orcinius Trojan has been discovered, employing VBA Stomping to hide its infection. The multi-stage trojan uses Dropbox and…
More than two-thirds (68%) of cyber-attacks are some outcome of human error or social engineering attack designed to target human frailties. As…
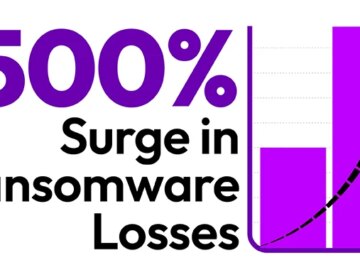
The cybersecurity threat landscape has witnessed a dramatic and alarming rise in the average ransomware payment, an increase exceeding 500%….
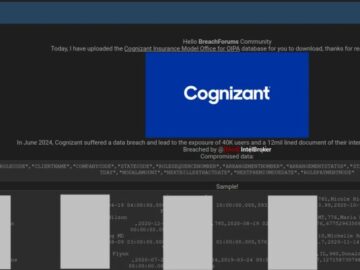
IntelBroker, a threat actor (TA) who is a prominent member of the notorious BreachForums, has allegedly leaked a trove of…
Prudential Financial data breach impacted over 2.5 million individuals Pierluigi Paganini July 02, 2024 Prudential Financial confirmed that more than…
Wise has warned some of its customers about a data breach at Evolve Bank & Trust, a bank they collaborated…