Rapid7, Inc., a leader in extended risk and threat detection, has announced a definitive agreement to acquire Noetic Cyber, a…
LogRhythm announced its 9th consecutive quarterly release. In the AI-ready world, LogRhythm empowers security teams with the highest integrity data…
Cisco has patched a critical zero-day vulnerability in its NX-OS software. The patched Cisco zero-day vulnerability was exploited in April…
Threat actors target IIS servers, as most of the internet-based crucial applications and services are installed on these servers. Hackers…
The Qualys Threat Research Unit has identified a newly discovered vulnerability in OpenSSH, dubbed “regreSSHion” (CVE-2024-6387). This critical flaw, which…
China-linked APT exploited Cisco NX-OS zero-day to deploy custom malware Pierluigi Paganini July 02, 2024 Cisco fixed an actively exploited…
Prudential Financial, a leading financial services company, has reported a data breach that has affected over 2.5 million individuals. The…
TeamViewer has confirmed that the cyberattack on its systems was orchestrated by Russian threat actors, specifically the APT29 or Midnight…
Jul 02, 2024NewsroomCyber Espionage / Vulnerability A China-nexus cyber espionage group named Velvet Ant has been observed exploiting a zero-day…
Thank you for joining! Access your Pro+ Content below. 2 July 2024 UKtech50 2024: The most influential people in UK…
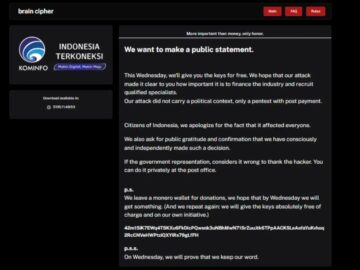
The notorious hacking group Brain Cipher has released decryption keys for free, allowing victims to recover their encrypted data without…
Jul 02, 2024NewsroomDigital Regulation / Tech News Meta’s decision to offer an ad-free subscription in the European Union (E.U.) has…