25 Jul Infosec Analyst Jobs: Six-Figure Salaries Posted at 08:52h in Blogs by Di Freeze This week in cybersecurity from…
“What we’re doing in transforming CCTV cameras into a powerful monitoring tool,” says Matthias Houllier, co-founder of Wintics, one of…
Single Sign-On (SSO) serves as the linchpin connecting corporate networks, facilitating seamless access to various web applications without the need…
Jul 25, 2024NewsroomCybercrime / Online Safety Meta Platforms on Wednesday said it took steps to remove around 63,000 Instagram accounts…
CISA has published the executive summaries from the Fall 2023 Joint SAFECOM-NCSWIC Bi-Annual Meeting, held in Cape Coral, Florida, from…
A hacktivist entity known as USDoD has claimed to have leaked CrowdStrike’s “entire threat actor list” and alleged possession of…
While the specifics for security testing vary for applications, web applications, and APIs, a holistic and proactive applications security strategy…
It is no secret that organizations globally are at risk of dealing with cyber threats every day that can jeopardize…
A research has claimed that Microsoft, which was involved in the global BSOD outage last week, is among the top…
Security analysts have identified 6,635 GeoServer instances exposed to the Internet, which makes them vulnerable to critical remote code execution…
Researchers have uncovered a vulnerability in Microsoft’s Windows Hello for Business (WHfB) that allows attackers to bypass its robust authentication…
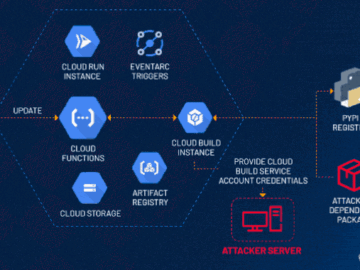
Jul 25, 2024NewsroomCloud Security / Vulnerability Cybersecurity researchers have disclosed a privilege escalation vulnerability impacting Google Cloud Platform’s Cloud Functions…