While cybercriminals are offering free tickets to Taylor Swift Eras Tour and other events, Ticketmaster is telling would-be purchasers that…
Hamas hacked into video streams from private security cameras in Israeli homes to gather intelligence before fighters descended on Israeli…
Evolve Bank & Trust (Evolve) is sending notices of a data breach to 7.6 million Americans whose data was stolen…
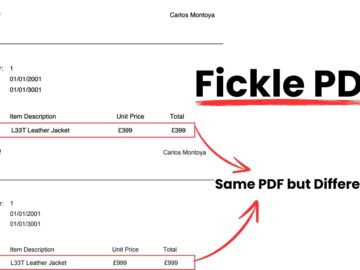
A cybersecurity researcher, Zakhar Fedotkin, demonstrated how differences in PDF rendering across various browsers and operating systems can be exploited…
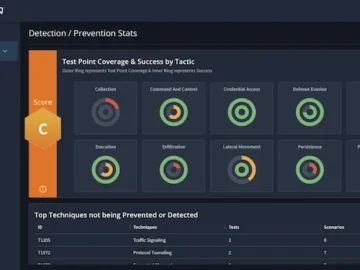
AttackIQ has introduced a new functionality for enterprise customers – AttackIQ Mission Control. AttackIQ Mission Control enhances AttackIQ Enterprise BAS…
Jul 09, 2024NewsroomVulnerability / Network Security Cybersecurity researchers have discovered a security vulnerability in the RADIUS network authentication protocol called…
Flash storage pioneer Pure Storage recently announced it will upgrade its Fusion control plane to make storage capacity in its…
DORA focuses on Information and Communications Technology (ICT) systems and applies to all financial institutions in the EU. This includes…
Countdown to October 2025 As the cybersecurity landscape continues to evolve and become more complex, international regulations are similarly following…
09 Jul Grappling With The Cybersecurity Talent Shortfall Posted at 08:48h in Blogs by Di Freeze This week in cybersecurity…
Lookout discovered GuardZoo, Android spyware targeting Middle Eastern military personnel. This campaign leverages malicious apps with military and religious themes…
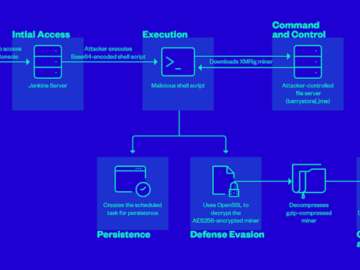
Jul 09, 2024NewsroomCI/CD Security / Server Security Cybersecurity researchers have found that it’s possible for attackers to weaponize improperly configured…