A critical vulnerability in PHP, tracked as CVE-2024-4577, is being actively exploited by threat actors in wild just days after…
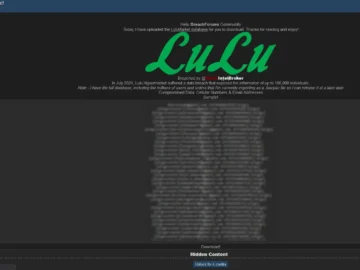
IntelBroker, a solo hacker on dark web forums, has claimed the LuLu Hypermarket data breach, targeting a prominent retail giant…
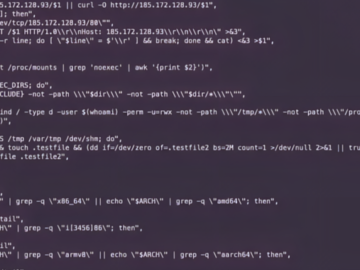
Jul 11, 2024NewsroomCyber Attack / Vulnerability Multiple threat actors have been observed exploiting a recently disclosed security flaw in PHP…
With terms like “AI washing” making their way into mainstream business consciousness, the hype surrounding AI is making it harder…
In this Help Net Security interview, Chaim Mazal, Chief Security Officer at Gigamon, discusses cybersecurity preparedness measures for businesses, the…
Jul 11, 2024NewsroomSoftware Security / Vulnerability GitLab has shipped another round of updates to close out security flaws in its…
This article compiles excerpts from various reports, presenting statistics and insights that could be helpful for CISOs. CISOs becoming more…
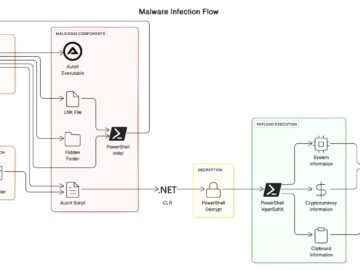
Researchers have observed improvements in the ViperSoftX info-stealing malware that had been first spotted in 2020. The malware has moved…
VMware fixed critical SQL-Injection in Aria Automation product Pierluigi Paganini July 11, 2024 VMware addressed a critical SQL-Injection vulnerability, tracked…
In the two weeks since the U.S. Supreme Court struck down a 40-year-old precedent that gave federal agencies wide latitude…
Non-profit Catholic Healthcare is using Microsoft’s holographic headset HoloLens to carry out telehealth appointments between residential care nurses and remote…
Over the last month, Microsoft 365 and Microsoft Office users have been experiencing “30088-27” errors when attempting to update the application….