1. Are You Prepared to Manage Incoming Vulnerability Reports? Naturally, the purpose of running a bug bounty program is to…
Kootenai Health, a prominent healthcare provider located at 2003 Kootenai Health Way, Coeur d’Alene, Idaho, has been the victim of…
APT42 (aka Damselfly, UNC788, CALANQUE, Charming Kitten) is a sophisticated Iranian state-sponsored cyber espionage group. This Advanced Persistent Threat (APT)…
The concept of “defense in depth” dates back to ancient times, epitomized by the ramparts, draw-bridge, towers, and battlements surrounding…
14 Aug Ransomware Trends In 2024: Larger Targets, Severe Losses, Devastating Downtime Posted at 09:06h in Blogs by Di Freeze…
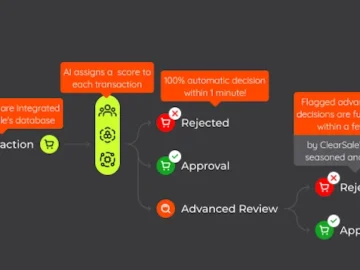
ClearSale has announced a new portfolio of fraud prevention tools designed to meet the evolving needs of today’s digital retail…
A coalition of law enforcement agencies coordinated by the U.K. National Crime Agency (NCA) has led to the arrest and…
Safety advocacy group The Dawn Project has ramped up its campaign to illustrate the failings of artificial intelligence (AI) systems…
A phishing email containing only a PNG image was sent from a compromised AWS account using the spoofed sender address…
In July 2022, Microsoft patched a well-known PPL bypass flaw, initially discovered by Ionescu and Forshaw. This allowed protection circumvention…
The Post Office is bringing in a new technology leader as it awaits additional government funding for its troubled programme…
Gigabud, an Android banking trojan impersonating government entities, initially targeted Thailand, the Philippines, and Peru. Its source code significantly overlaps…
![Is Your Security Ready For Bug Bounty? [5 Questions] Hackerone logo](https://image.cybernoz.com/wp-content/uploads/2024/08/Is-Your-Security-Ready-For-Bug-Bounty-5-Questions-360x270.png)