Hackers have claimed that the personal data of 8 million customers of Angel One, a prominent broking house, has been…
Ransomware-as-a-service (RaaS) has evolved into sophisticated enterprise-like model. From 2022 to 2023, ransomware programs advertised on the dark web increased…
Australia isn’t alone! The Five Eyes (US, UK, Canada, NZ) along with Japan and South Korea join forces to blame…
Jul 10, 2024The Hacker NewsEndpoint Security / Identity Security It’s the age of identity security. The explosion of driven ransomware…
Google has announced the integration of passkeys into its Advanced Protection Program (APP). This development aims to provide an easier…
The recent cyber attack on the Ministry of Defence, which compromised the personal information of UK military personnel, serves as…
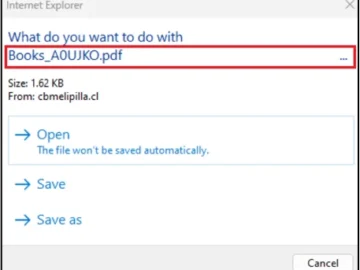
CVE-2024-38112, a spoofing vulnerability in Windows MSHTML Platform for which Microsoft has released a fix on Tuesday, has likely been…
Jul 10, 2024NewsroomEndpoint Security / Vulnerability Microsoft has released patches to address a total of 143 security flaws as part…
Microsoft’s July 2024 Patch Tuesday has brought a significant wave of updates, addressing a total of 139 vulnerabilities across various…
The Problem The “2024 Attack Intelligence Report” from the staff at Rapid7 [1] is a well-researched, well-written report that is…
Sharp Europe sells electronic devices, appliances and equiment both to people at home and to businesses. Its business offerings have…
CISA has added two zero-day vulnerabilities from the cluster of vulnerabilities fixed in this month’s patch Tuesday. In its latest…