Wiz, the $12 billion cloud security startup, has rejected a $23 billion acquisition offer from Google parent Alphabet. Fortune viewed…
Lvivteploenergo didn’t respond to WIRED’s request for comment, nor did the SBU. Ukraine’s cybersecurity agency, the State Services for Special…
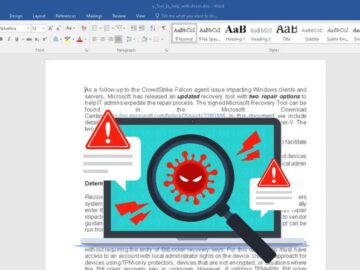
Threat actors have been found exploiting a recently discovered bug in CrowdStrike’s software that causes a Blue Screen of Death…
Normal0 falsefalsefalse EN-US /* Style Definitions */table.MsoNormalTable{mso-style-name:”Table Normal”;mso-tstyle-rowband-size:0;mso-tstyle-colband-size:0;mso-style-noshow:yes;mso-style-priority:99;mso-style-parent:””;mso-padding-alt:0in 5.4pt 0in 5.4pt;mso-para-margin:0in;mso-pagination:widow-orphan;mso-hyphenate:none;font-size:10.0pt;mso-bidi-font-size:11.0pt;font-family:”Calibri”,sans-serif;mso-ascii-font-family:Calibri;mso-ascii-theme-font:minor-latin;mso-hansi-font-family:Calibri;mso-hansi-theme-font:minor-latin;mso-bidi-font-family:Calibri;mso-bidi-theme-font:minor-bidi;mso-font-kerning:1.0pt;mso-ligatures:standardcontextual;} The 2024 Paris Olympic Games, set to begin later…
As organizations increasingly adopt third-party AI tools to streamline operations and gain a competitive edge, they also invite a host…
Jul 23, 2024NewsroomOnline Privacy / Regulatory Compliance Google on Monday abandoned plans to phase out third-party tracking cookies in its…
Thank you for joining! Access your Pro+ Content below. 23 July 2024 Serving up a GenAI experience at Wimbledon Share…
Wiz, the Israeli cybersecurity firm, has made a strategic decision to reject a staggering $23 billion acquisition offer from Google’s…
Uninterrupted flow of power is essential for delivering critical services across the public sector, such as healthcare, emergency responses, and…
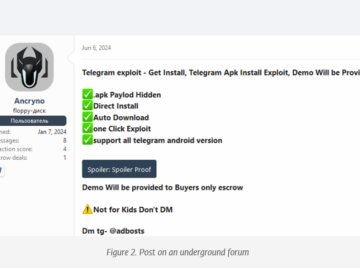
EvilVideo, a Telegram Android zero-day allowed sending malicious APKs disguised as videos Pierluigi Paganini July 22, 2024 EvilVideo is a…
The Land Registry agency in Greece has announced that it suffered a limited-scope data breach following a wave of 400…
As the world prepares for the start of the Paris Olympics later this week, athletes and spectators alike are filled…