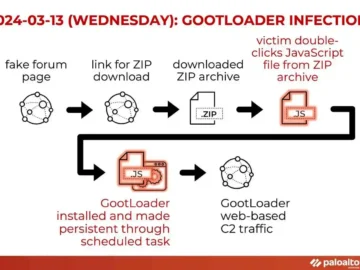
GootLoader, a sophisticated JavaScript-based malware has continued to challenge cybersecurity experts with its unique evasion techniques. However, researchers have discovered…
The cybercriminals who claimed responsibility for the Ticketmaster data breach say they’ve stolen 440,000 tickets for Taylor Swift’s Eras Tour….
Internet giant Cloudflare reports that its DNS resolver service, 1.1.1.1, was recently unreachable or degraded for some of its customers…
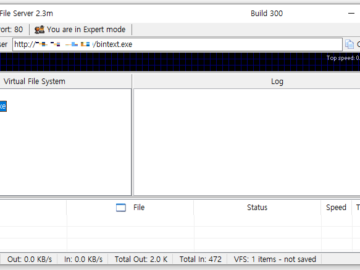
Malicious actors are targeting HTTP File Servers (HFS) from Rejetto by leveraging vulnerabilities to deploy malware and cryptocurrency mining software….
Hackers have leaked what they claim is Ticketmaster barcode data for 166,000 Taylor Swift Eras Tour tickets, warning that more…
Europol’s recent paper sheds light on formidable challenges posed by Privacy Enhancing Technologies (PET) in Home Routing systems. These technologies,…
Security breach potentially exposed internal secrets at AI research firm OpenAI after hackers accessed discussions on sensitive AI projects in…
A new ransomware-as-a-service (RaaS) called Eldorado emerged in March and comes with locker variants for VMware ESXi and Windows. The gang…
Airtel, also known as Bharti Airtel, has denied reports of a data breach following speculation from various media outlets. The…
05 Jul From Hacking Into Banks To Protecting Them, A Redemption Story Posted at 09:52h in Blogs by Di Freeze…
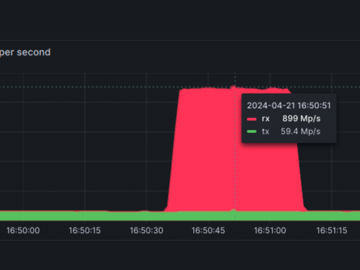
Jul 05, 2024NewsroomNetwork Security / DDoS Attack French cloud computing firm OVHcloud said it mitigated a record-breaking distributed denial-of-service (DDoS)…
As online shoppers ready themselves for the approaching Amazon Prime Day on July 16-17, 2024, a day known for unusually…