A sophisticated attack technique that exploits Microsoft’s OneDrive application through DLL sideloading, allowing threat actors to execute malicious code while…
The Cybersecurity and Infrastructure Security Agency has issued an urgent alert about a critical command-injection vulnerability in Control Web Panel…
As humanoids reach new levels of maturity, their use in complex operational environments is moving much closer to the mainstream….
The U.S. Treasury Department imposed sanctions on two North Korean financial institutions and eight individuals involved in laundering cryptocurrency stolen…
Microsoft has issued an urgent advisory for Windows users, highlighting a potential glitch that could force certain devices into the…
A critical vulnerability discovered in the AI Engine WordPress plugin threatens over 100,000 active installations worldwide. On October 4th, 2025,…
Crowdsourced cyber security firm Bugcrowd hopes to make good on a plan to “unite the hacker community and the power…
A significant security threat has emerged from the Google Play Store, where threat actors have successfully deployed 239 malicious applications…
European organizations are facing an unprecedented surge in ransomware attacks as cybercriminals increasingly adopt artificial intelligence and sophisticated social engineering…
The marketplace revolution is here, and it’s transforming how we buy, sell, and share everything from vintage furniture to professional…
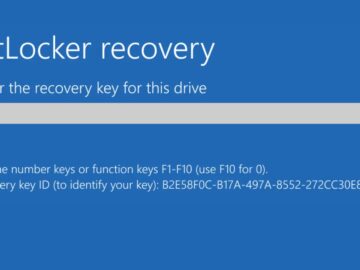
Microsoft has warned that some systems may boot into BitLocker recovery after installing the October 2025 Windows security updates. BitLocker…
Two cybersecurity professionals have been federally charged for orchestrating a sophisticated ransomware campaign targeting multiple American businesses. Ryan Clifford Goldberg,…