About 12.9 million Australians are impacted by the breach of defunct electronic prescription provider MediSecure, with 6.5TB of personal and…
Dark web monitoring is essential for CEOs in the banking industry to combat the escalating threat of cybercrime. In 2023,…
Google will infuse artificial intelligence into the US broadcast of the Paris Olympics, allowing sports commentators to use AI to…
A cybercriminal gang that researchers track as Revolver Rabbit has registered more than 500,000 domain names for infostealer campaigns that…
ANZ Banking Group is starting to see some uneven benefits distribution from its use of AI pair programming, with training…
A US judge dismissed most of a Securities and Exchange Commission lawsuit accusing software company SolarWinds of defrauding investors by…
Although not new, Registered Domain Generation Algorithms (RDGAs) have become a major cybersecurity threat, exploited by threat actors to bypass…
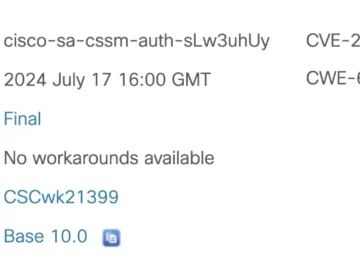
Cisco has issued a critical security advisory for a vulnerability in its Cisco Smart Software Manager On-Prem licensing tool, which…
The growing normalisation of the widespread storing and sharing of self-created intimate images in the UK is heightening the risk…
Hackers exploit browser injectors to manipulate web content, steal sensitive information, and hijack user sessions. By injecting malicious code into…
Microsoft, the American technology giant, has issued a warning regarding a newly identified cybercrime group known as Octo Tempest. This…
A former detective regarded as a key witness in an investigation into allegations that police unlawfully monitored the phones of…