Russian businessman sentenced to 3 years for smuggling military-grade microelectronics to Russia via Hong Kong. Maxim Marchenko used shell companies…
Recent cybersecurity incidents affecting auto dealerships nationwide have underscored the growing importance of strong security measures. United States government organizations…
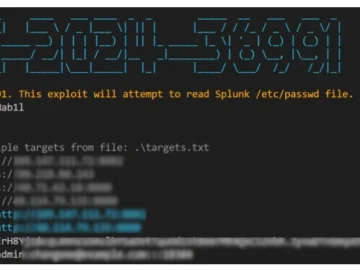
A recently fixed vulnerability (CVE-2024-36991) affecting Splunk Enterprise on Windows “is more severe than it initially appeared,” according to SonicWall’s…
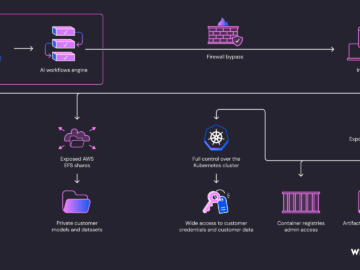
SAPwned flaws in SAP AI core could expose customers’ data Pierluigi Paganini July 18, 2024 Researchers discovered security flaws in SAP…
Microsoft has fixed a known issue preventing the Microsoft Photos app from starting on some Windows 11 22H2 and 23H2…
In one of the largest cyber breaches in Australian history, MediSecure, a former provider of digital prescriptions, has revealed that…
Hackers exploit open-source tools to execute attacks because they are readily available, well-documented, and often have extensive community support, making…
Business Email Compromise (BEC) is a social engineering scam where attackers impersonate legitimate business emails to defraud employees, partners, and…
Jul 18, 2024NewsroomOpen-Source / Cybercrime Unknown threat actors have been observed leveraging open-source tools as part of a suspected cyber…
The government trusted the views of the Post Office over allegations by subpostmasters that they were being mistreated over unexplained…
Major sporting events with massive online audiences, like the World Cup and Olympics, have become magnets for cyberattacks, which are…
DeepKeep, the leading provider of AI-Native Trust, Risk, and Security Management (TRiSM), empowers large corporations that rely on AI, GenAI,…