In November 2023, hackers from Iran hacked the Municipal Water Authority of Aliquippa, Pennsylvania. They targeted a vulnerable control system…
There is a grand tradition at the annual Defcon security conference in Las Vegas of hacking ATMs. Unlocking them with…
A sophisticated phishing campaign targeting Windows systems leverages multiple evasion techniques, including Python obfuscation, shellcode generation, and loading, to deploy…
For many, this news might seem trivial as it doesn’t involve direct harm to humans. However, the recent death of…
09 Aug Former White House CIO Theresa Payton Shares Election Security Insights Posted at 08:57h in Blogs by Di Freeze…
A “0.0.0.0-Day” vulnerability affecting Chrome, Safari and Firefox can be – and has been – exploited by attackers to gain…
Electronic surveillance equipment provider ADT filed a form 8-K with the Security and Exchange Commision (SEC) to report “a cybersecurity…
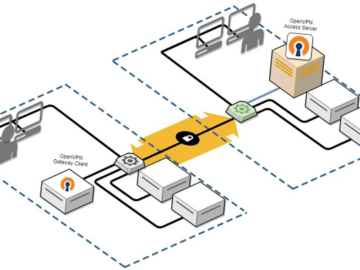
Aug 09, 2024Ravie LakshmananVulnerability / Network Security Microsoft on Thursday disclosed four medium-severity security flaws in the open-source OpenVPN software…
Imagine waking up one day to find that all your confidential emails are suddenly an open book for anyone with…
The healthcare sector, with its vast repositories of sensitive patient information, has become a prime target for cybercriminals. According to…
Elon Musk’s X, formerly known as Twitter, has agreed to temporarily halt the collection and processing of personal data from…
Five zero-days impacts EoL Cisco Small Business IP Phones. Replace them with newer models asap! Pierluigi Paganini August 09, 2024…