Apple has announced the launch of a “groundbreaking cloud intelligence system” called Private Cloud Compute (PCC) that’s designed for processing…
Recent high-profile data leaks, including incidents involving Santander and Ticketmaster, have highlighted the ongoing issue of data breaches affecting a…
Cisco, a global leader in networking and cybersecurity solutions, has announced the appointment of Sean Duca as its new Chief…
“We’re about to see a revolution in space. Very few people have even grasped how much of a revolution it’s…
Jun 11, 2024NewsroomMalware / Cyber Attack Cybersecurity researchers have uncovered an updated version of malware called ValleyRAT that’s being distributed…
Switzerland has seen a notable increase in cyberattacks and disinformation campaigns as it prepares to host a crucial summit aimed…
AGL Energy is set to overhaul its consumer business operations through a 20 percent stake in electricity supply and billing…
Expert released PoC exploit code for CVE-2024-29849. Patch it now! Pierluigi Paganini June 11, 2024 A proof-of-concept (PoC) exploit code…
Security analysis identified multiple vulnerabilities in the Netgear WNR614 JNR1010V2 N300 router (firmware V1.1.0.54_1.0.1) that could allow attackers to bypass…
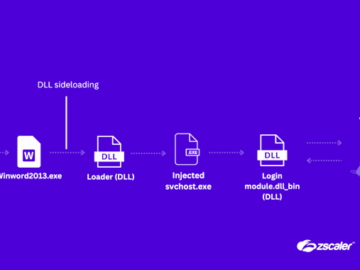
Hackers utilize MSC or Microsoft Management Console files in themed attack campaigns as these files contain commands and scripts that…
Thank you for joining! Access your Pro+ Content below. 11 June 2024 Drilling into data to help the UK’s energy…
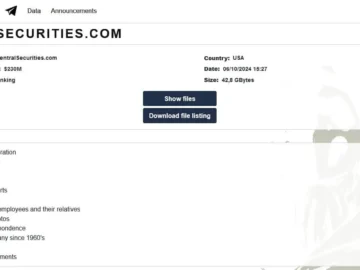
The Underground Team ransomware group has allegedly claimed a cyberattack on Central Securities Corporation, asserting access to a staggering 42.8…