Jun 20, 2024NewsroomCyber Espionage / Critical Infrastructure Cyber espionage groups associated with China have been linked to a long-running campaign…
Campaigner Sir Alan Bates has hit out at the “utter incompetence” of Post Office bosses after he learned that a…
A newly discovered security vulnerability allows attackers to impersonate Microsoft corporate email accounts, significantly increasing the risk of phishing attacks….
Fortinet’s FortiGuard Labs discovered a Rust-based stealer in May 2024 and named it the Fickle Stealer due to its intricate…
The recent cyberattacks affecting water treatment plants and systems across the nation shed light on the need for cybersecurity measures…
Jun 20, 2024The Hacker NewsEndpoint Protection / Data Security Highlights Complex Tool Landscape: Explore the wide array of cybersecurity tools…
CISA has released the new version of the SAFECOM Guidelines. This exclusive guideline talks about the Emergency Communications Grants in…
The question is not ‘if’ your organization will face a cybersecurity threat but ‘when.’ The bad news gets worse: suffering…
CDK Global, a software-as-a-service (SaaS) provider for car dealers and auto equipment manufacturers, has suffered a cyberattack that has temporarily…
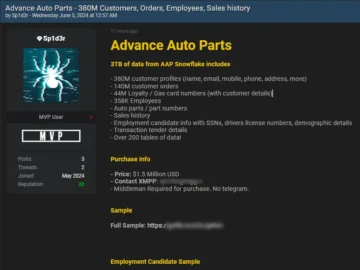
Advance Auto Parts, Inc., one of the big suppliers of automobile aftermarket components in America, has reported a data breach…
The popular corporate messaging platform Slack has warned its Russian users that their accounts will be suspended within 30 days,…
The Federal Trade Commission (FTC) has announced it’s referred a complaint against TikTok and parent company ByteDance to the Department…