Cybersecurity and infosecurity professionals say that work-related stress, fatigue, and burnout are making them less productive, including taking extended sick…
A coding error in an access control allegedly left an API open to abuse, facilitating the Optus data breach, according…
T-Mobile has denied it was breached or that source code was stolen after a threat actor claimed to be selling…
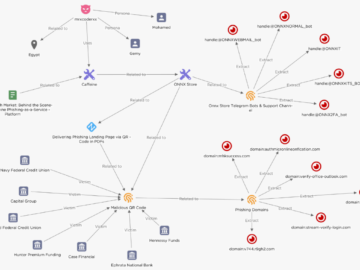
Researchers have discovered a new phishing campaign that relies on a phishing-as-a-service platform called ONNX Store, available for purchase over…
Australia Post is tightening up remote access security for employees and third parties as it renews a cloud hosting agreement…
Alleged researchers stole $3 million from Kraken exchange Pierluigi Paganini June 19, 2024 Alleged researchers have exploited a zero-day in…
Image: DigitalIceAge Forklift manufacturer Crown Equipment confirmed today that it suffered a cyberattack earlier this month that disrupted manufacturing at its…
Bayer’s crop science division is increasingly turning to artificial intelligence in its battle against crop killing weeds, the company told…
Advanced Micro Devices (AMD) is looking into claims that the company’s data was stolen in a hack by a cybercriminal…
Two weeks after the Australian privacy watchdog filed a lawsuit against Medibank for failure to protect personal information of its…
A new threat actor group called Void Arachne is conducting a malware campaign targeting Chinese-speaking users. The group is distributing…
Dell Technologies is assembling half of the racks for the supercomputer that xAI is building, billionaire Elon Musk said in…