Northern Beaches Council is undertaking a thorough assessment of its technology and capability stack to secure its 50-plus business units….
Defence is set to run a “feasibility trial” of four containerised computer rooms that could make life easier for IT…
NAB’s ambitions to use generative AI as a tool in the fight against financial crime are being curtailed by rules…
Startup Character.AI said it has signed an agreement with Alphabet’s Google that grants the search engine giant a non-exclusive license…
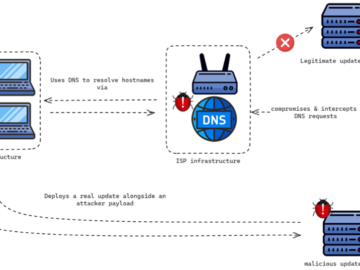
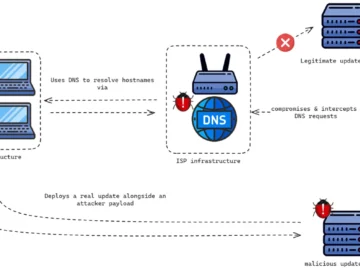
Chinese StormBamboo APT compromised ISP to deliver malware Pierluigi Paganini August 04, 2024 A China-linked APT, tracked as StormBamboo, compromised an…
A massive Magniber ransomware campaign is underway, encrypting home users’ devices worldwide and demanding thousand-dollar ransoms to receive a decryptor….
Stay up to date with cybersecurity news! Our Weekly Cybersecurity Newsletter provides a curated summary of the most important updates,…
Data security and consumer trust go hand-in-hand in our evolving digital world There’s no doubt that data is a catalyst…
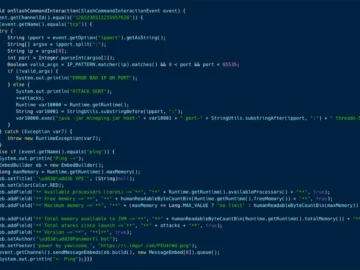
A new Distributed Denial of Service (DDoS) campaign, named “Panamorfi,” operated by the threat actor yawixooo exploits misconfigured Jupyter notebooks…
Hackers attempt to sell the personal data of 3 billion people resulting from an April data breach Pierluigi Paganini August…
The SLUBStick cross-cache attack has emerged as a groundbreaking method for exploiting vulnerabilities in the Linux kernel. Discovered by researchers…
A sophisticated hacking group by the name of StormBamboo has successfully compromised an internet service provider (ISP) to launch a…