Fraudsters leverage complex phishing scams in attempt to gain control over organizations’ Meta accounts A sophisticated phishing campaign is targeting…
Dutch independent research firm TNO is working with the National Cyber Security Centre (NCSC) to investigate future topics and developments…
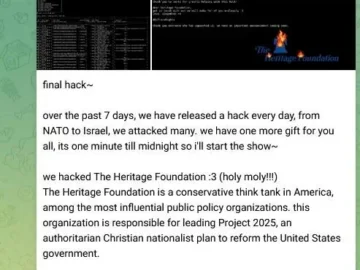
SiegedSec, who describe themselves as “gay furry hackers,” claimed responsibility for a cyberattack on The Heritage Foundation before the hacktivist group…
Scammers are leveraging deepfake technology to create convincing health and celebrity-endorsed ads on social media, targeting millions globally. Learn how…
11 Jul Deep Observability Wanted By CISOs And Corporate Boards Posted at 08:44h in Blogs by Di Freeze This week…
Do you use Authy for your multi-factor authentication needs? If you do, you should keep an eye out for phishing…
Jul 11, 2024NewsroomCyber Espionage / Network Security The China-linked advanced persistent threat (APT) group codenamed APT41 is suspected to be…
The Cloud Infrastructure Service Providers in Europe (CISPE) trade body stands accused of selling its members down the river, after…
Hacktivist groups have intensified their efforts to launch cyberattacks on the NATO 75th Anniversary Summit in Washington, DC, taking place…
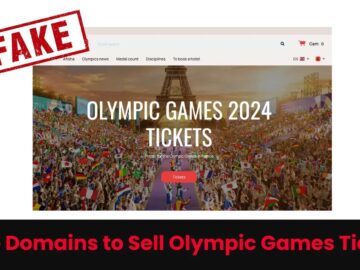
As the world eagerly anticipates the Olympic Games Paris 2024, a cybersecurity threat has emerged, targeting fans and attendees. Cybersecurity…
Kubernetes is 10! Mid-2024 sees the 10th birthday of the market-leading container orchestration platform. But, according to DataStax developer relations guy…
Jul 11, 2024The Hacker NewsCompliance / Identity Management Today, all organizations are exposed to the threat of cyber breaches, irrespective…