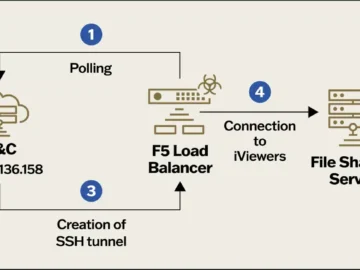
Researchers that were called to investigate a cyberattack on a large organization in late 2023 have traced the activity to…
VMware has issued a security advisory addressing critical vulnerabilities in vCenter Server, including remote code execution and local privilege escalation flaws….
The notorious threat actor known as Intelbroker claims to have orchestrated a massive data breach of AMD, a top player…
A scathing report by Australia’s Information Commissioner details how misconfigurations and missed alerts allowed a hacker to breach Medibank and steal…
Sometimes you’ll see the term “overlays” used in articles about malware and you might wonder what they are. In this…
Experts slammed the latest European Union proposals for chat control to prevent child sexual abuse calling it a front face…
VMware fixed RCE and privilege escalation bugs in vCenter Server Pierluigi Paganini June 18, 2024 VMware addressed vCenter Server vulnerabilities…
The Kansas City, Kansas Police Department (KCKPD) is facing a major security breach after the notorious BlackSuit ransomware group leaked…
Jun 18, 2024NewsroomPrivacy / Encryption A controversial proposal put forth by the European Union to scan users’ private messages for…
Internet Computer Protocol (ICP), a decentralized blockchain network that extends the functionality of Web3 by overcoming the limitations of traditional…
An independent fund, imec.xpand, is benefiting from a partnership with Belgian research giant imec to find the right investments and…
The Federal Trade Commission has filed a complaint in US federal court against Adobe and two executives, Maninder Sawhney and…