Guidehouse Inc., based in McLean, Virginia, and Nan McKay and Associates, headquartered in El Cajon, California, have agreed to pay…
A recently identified ransomware variant dubbed OPIX encrypts user files using a random character string and adds the “.OPIX” extension…
On June 13, 2024, the Cybersecurity and Infrastructure Security Agency (CISA) made history by conducting the federal government’s inaugural tabletop…
Software security requires a creative and disciplined approach. It involves having the vision to develop secure strategy, tactics, and execution….
Jun 18, 2024NewsroomNetwork Security / Vulnerability VMware has released updates to address critical flaws impacting Cloud Foundation, vCenter Server, and…
As the adage goes, if you give a man a fish, he can eat for a day, but if you…
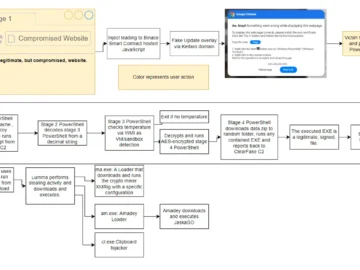
Cybersecurity researchers have uncovered a disturbing trend in malware delivery tactics involving sophisticated social engineering techniques. These methods exploit user…
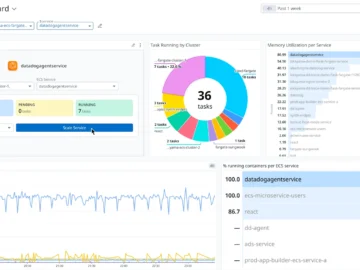
Datadog launched Datadog App Builder, a low-code development tool that helps teams create self-service applications and integrate them securely into…
Jun 18, 2024NewsroomMobile Security / Financial Fraud The Singapore Police Force (SPF) has announced the extradition of two men from…
Thank you for joining! Access your Pro+ Content below. 18 June 2024 General election 2024 – the digital policies examined…
In a joint effort to enhance election security and public confidence, the Cybersecurity and Infrastructure Security Agency (CISA) and the…
The Financial Dynamics Behind Ransomware Attacks Pierluigi Paganini June 18, 2024 Over the last few years, ransomware attacks have become…