Panera Bread, known for its bakery products, reportedly succumbed to ransomware hackers’ demands following an attack in March 2024. The…
The Los Angeles County Department of Public Health (DPH) has disclosed a significant data breach impacting more than 200,000 individuals….
Hackers often focus on F5 Load Balancers for several reasons, as these are many enterprise networks’ vital parts that balance…
Memory corruption lets attackers hijack control flow, execute code, elevate privileges, and leak data. ARM’s Memory Tagging Extension (MTE) aims…
Cybersecurity isn’t just about firewalls and antivirus. It’s about understanding how your defenses, people, and processes work together. Just like…
In this Help Net Security interview, Alan DeKok, CEO at NetworkRADIUS, discusses the need for due diligence in selecting and…
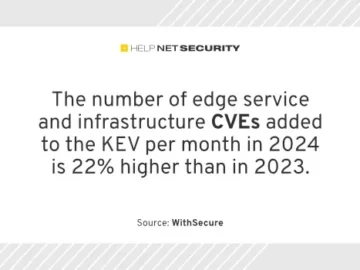
The cyber threat landscape in 2023 and 2024 has been dominated by mass exploitation, according to WithSecure. Edge service KEV…
While 75% of enterprises are implementing AI, 72% report significant data quality issues and an inability to scale data practices,…
The US government has sued Adobe, accusing the Photoshop and Acrobat maker of harming consumers by concealing hefty termination fees…
A new malware distribution campaign uses fake Google Chrome, Word, and OneDrive errors to trick users into running malicious PowerShell…
Three out of Vietnam’s five active international undersea internet cables are down, state media said, the second major round of…
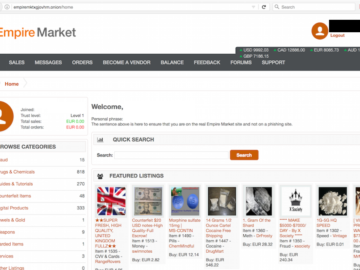
Empire Market owners charged with operating $430M dark web marketplace Pierluigi Paganini June 17, 2024 Federal authorities charged two individuals…