78% of organizations are tracking AI as an emerging risk while simultaneously adopting the technology themselves, according to AuditBoard. Organizations…
Hackers often monitor web activities to gather several types of confidential data. By tracking your online activities, hackers can tailor…
An unauthenticated endpoint vulnerability allowed threat actors to identify phone numbers associated with Authy accounts, which was identified, and the…
Here’s a look at the most interesting products from the past week, featuring releases from LogRhythm, NordVPN, Regula, and Scythe….
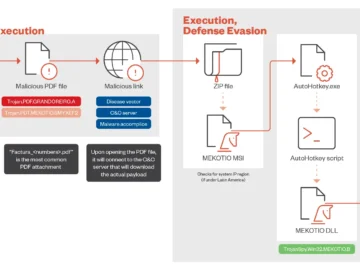
The Mekotio banking trojan has resurfaced as a significant threat to financial institutions and individuals across Latin America. The Mekotio…
The ShinyHunters hacker group claims the Ticketmaster breach is far bigger than previously anticipated, stealing 193 million barcodes, including 440,000…
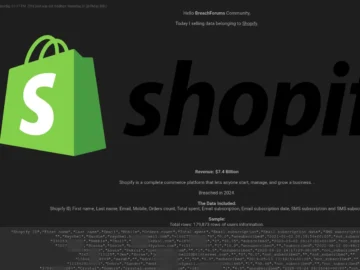
A known threat actor on the BreachForums who uses the moniker ‘888’ has shared data allegedly stolen from Shopify in…
AI. Artificial Intelligence. One acronym, two words that seem to have reshaped the landscape of cybersecurity. At the 2024 RSA…
According to cybersecurity researchers at Halcyon AI, the new Volcano Demon ransomware gang calls its victims “very frequently, almost daily…
Services Australia will spend almost $94 million to renew longstanding licensing and support agreements with VMware for another three years….
A senior executive at Chinese technology giant Huawei has dismissed the idea that a shortage of the most advanced artificial…
OVHcloud mitigated a record-breaking DDoS attack in April 2024 Pierluigi Paganini July 04, 2024 OVHcloud successfully mitigated a record-breaking DDoS…