Queensland public sector projects will soon be subject to internal assessments and external reviews designed for evaluating and mitigating risks…
PLANETVPN.EXE Information This is a valid program but it is not required to run on startup. This program is not…
The Department of Defence has called in outside help for business readiness testing around the financial portion of its long-running…
KEEPASSXC.EXE Information This is a valid program but it is not required to run on startup. This program is not…
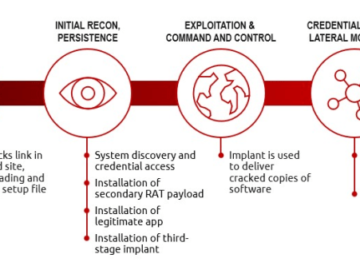
The UK’s National Crime Agency (NCA), together with partner agencies from around the world, including the FBI and agencies from…
Australia’s eSafety Commissioner has given key online industry players six months to develop “enforceable codes” to shield children from exposure…
Healthcare fintech firm HealthEquity is warning that it suffered a data breach after a partner’s account was compromised and used…
According to the Office of the Comptroller of the Currency, “Financial crime threatens the safety and soundness of financial systems…
PARSECD.EXE Information This is a valid program but it is not required to run on startup. This program is not…
Last year was a brutal year in the cybersecurity field. Technologies like generative AI introduced new attack vectors to already…
Operation Morpheus took down 593 Cobalt Strike servers used by threat actors Pierluigi Paganini July 03, 2024 An international law…
OVHcloud, a global cloud services provider and one of the largest of its kind in Europe, says it mitigated a…